Grounded in Infrastructure
Focused on Cloud
Security Information Architect with deep expertise in cloud and on-premise environments, specialising in engineering, governance, audit compliance, and vulnerability remediation within regulated sectors.

Cyber Security Specialist
Cyber Security project delivery across Azure cloud environments.
Cloud Security
Delivery of robust protection and resilience across Azure and Microsoft cloud environments.
GRC Expertise
Outcome-focused GRC expert aligning security with business goals, compliance, and real-world resilience.
CNI Experience
Assuring high-stakes environments through structured risk management and defensible architecture.
Audit & Control Validation
Evidencing control maturity for internal audits, regulatory assessments, and external certifications.
Threat Detection Readiness
Microsoft Defender Suite and KQL-driven insights to stay ahead of emerging threats.
Security Strategy & Engagement
Translating complex security challenges into board-level outcomes with clarity and confidence.
Audio Introduction
Listen to a brief overview of my background and approach.
About Me
20+ years Engineering, Architecting and securing on-prem and cloud infrastructure with deep cybersecurity expertise. Specialising in business-driven GRC frameworks that deliver scalable, resilient security solutions.
Expertise
Cloud security architecture, compliance automation, security operations, and risk management. Experience spans multiple sectors, driving enterprise-grade cyber security initiatives.
My Approach
Security should enable progress, not hinder it. I embed practical security early, aligning with GRC to ensure secure, compliant, and operationally fit systems.
Key Skills
Cloud Security Engineering,Architecture (Azure & Microsoft 365), GRC, AI Security Governance, Technical Security Control Design, Implementation, and Cybersecurity Project Leadership.
Technical Skills
Specialised technical expertise across cloud platforms, security tools, and infrastructure technologies.
Cloud Technologies
Microsoft Azure
Microsoft 365
Security Frameworks
Tech Stack
GRC
- Policy, Standards, Procedures
- Risk Assessments & Treatment
- Information Security Policy
- Controls Testing & Framework Alignment
SIEM & Monitoring
- Microsoft Sentinel
- Tenable One
- Azure Monitor & Log Analytics
- KQL Query Language
Endpoint Security
- Microsoft Defender for Endpoint (MDE)
- Microsoft Purview
- Data Loss Prevention (DLP)
- Intune MDM & WDAC
Infrastructure & Automation
Infrastructure as Code
- Azure Resource Manager (ARM)
- Automated Patch Management
- CIS-Hardened Builds
Scripting
- PowerShell,, Logic Apps
- BASH \ Python
- SQL, KQL
Reporting
- Power BI
- Power Automate
- AI Prompt Engineering
Professional Projects
A track record of successful security project outcomes.
Cyber Security Specialist
Sizewell C | Nuclear CNI
- Engage with internal and external partners to ensure services are secure by design.
- Audit vulnerabilities and provide actionable mitigation strategies.
- Conduct security reviews, risk assessments, and audits.
- Ensure compliance alignment with recognised industry frameworks.
- SC Cleared - Comfortable working in Highly Regulated Environments.
Security Consultant
Northern Power Grid | Electricity CNI
- Endpoint security controls within OT pre-production environment using Carbon Black EDR.
- Authored (HLD/LLD) security designs, contributing to defensible architecture.
- Delivered tailored application control baselines and custom EDR rule sets.
- Mentored internal teams on secure operations, post-project handover.
Infrastructure Security Engineer
Ineos Oil & Gas | Oil & Gas
- Delivery of a NIST-aligned cyber security program across IT and OT infrastructure.
- Oversaw onboarding of MSSP, SIEM (Dell SecureWorks), and tuning of IDS/IPS policies.
- Deployed enterprise EDR, DNS security (Carbon Black, Cisco Umbrella), and IAM controls (OKTA).
- Azure and O365 security architecture with hardened image deployments and automated patching.
- Projects delivered despite the covid shutdown.
Infrastructure Security Engineer
Kobalt Music Publishing | Media & Entertainment
- Deployed global EDR and SIEM solutions (Carbon Black, Splunk), enhancing detection and response.
- Onboarded IAM solutions (OKTA) and drove secure integration with AWS, Confluence, and JIRA.
- Hardened systems using CIS benchmarks, with automation of secure Windows 10 builds.
- Developed and enforced global security policies, procedures, and vulnerability management processes.
Network Systems Analyst
ACCOR Hotels UK & Ireland | Global Hospitality
- Delivered secure infrastructure support across 250+ sites during a major digital transformation, contributing to PCI DSS compliance across UK & European hotel networks.
- Migrated legacy Exchange to Office 365, enabling secure and scalable email infrastructure.
- Decommissioned legacy VPNs and coordinated secure firewall upgrades across 200+ Cisco devices.
- Implemented secure scripting, patching automation, and compliance monitoring using PowerShell, SCCM, and event log auditing.
Open Source Contributions
Loading live data from GitHub...
Explore More Resources
Dive deeper into cybersecurity implementations, live monitoring, and expert guidance.
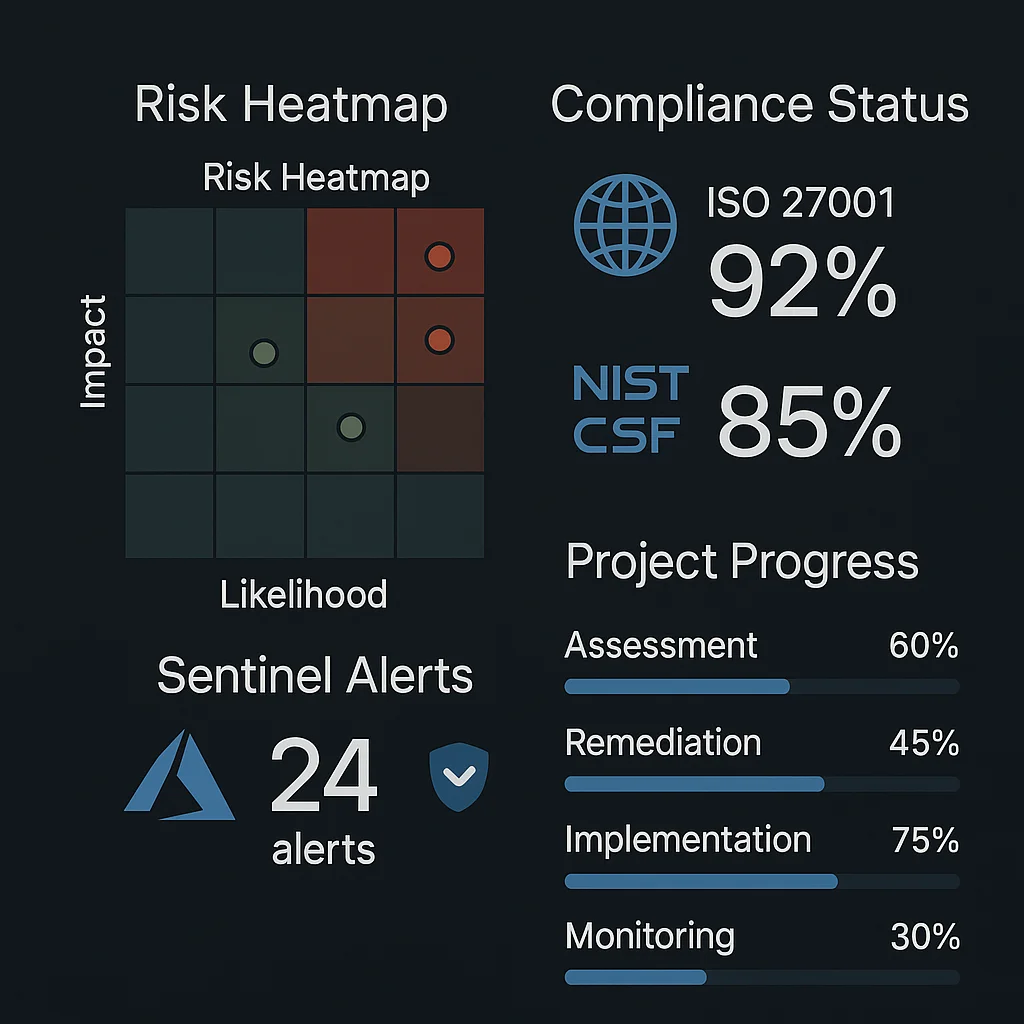
Live Security Dashboard
Interactive security operations center showcasing real-time threat intelligence and compliance monitoring.
- Real-time threat detection metrics
- Compliance framework tracking
- Infrastructure health monitoring
- Executive-level security reporting
Project Gallery
Visual showcase of cybersecurity implementations, security architecture diagrams, and project outcomes.
- Security architecture diagrams
- Compliance framework mappings
- Threat intelligence dashboards
- Real-world implementation examples
Expert FAQ
Comprehensive answers to common cybersecurity questions covering implementation strategies and best practices.
- Cloud security implementation
- GRC framework guidance
- Compliance requirements
- Security architecture decisions
Get in Touch
Interesting projects?
Get in touch to discuss how I can help in designing and implementing effective security controls across cloud environments and implementing effective GRC.
Contact Me
Get in touch to discuss your cybersecurity needs or ask questions about my services.